[+]Add: search_exploits
This commit is contained in:
2
.gitignore
vendored
2
.gitignore
vendored
@@ -8,3 +8,5 @@ __pycache__/
|
||||
|
||||
*.xml
|
||||
*.iml
|
||||
*.log
|
||||
.vscode/settings.json
|
||||
|
||||
10
README.md
10
README.md
@@ -123,3 +123,13 @@
|
||||
- js代码中敏感信息收集 # 主要参考 <https://threezh1.github.io> By Threezh1
|
||||
|
||||
> moon.py -u js <http://xxx.xxx.xxx.xxx:xxxx>
|
||||
|
||||
## search_exploits
|
||||
|
||||
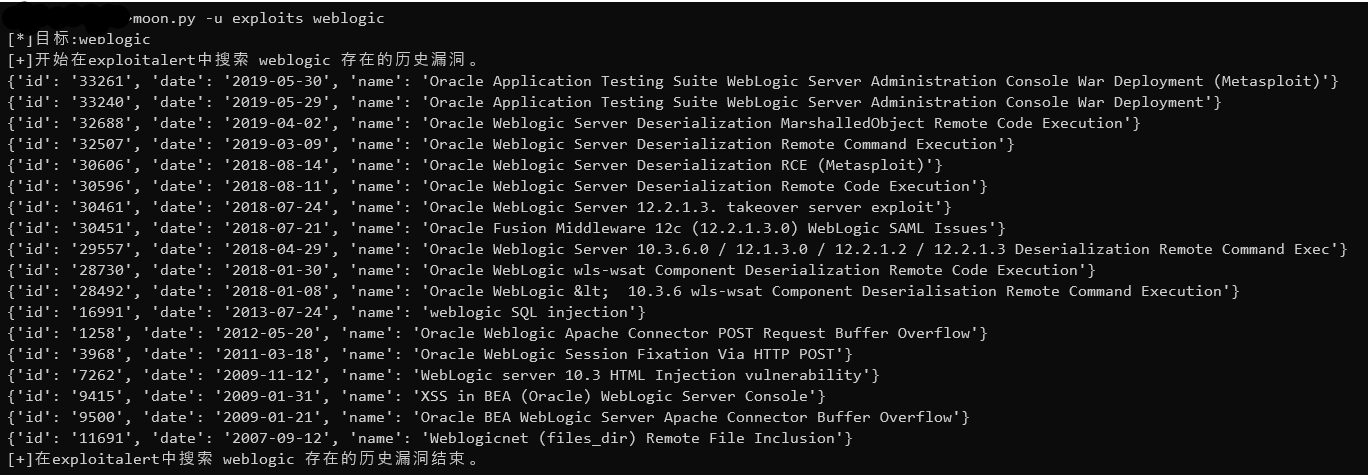
- 在 exploitalert 中搜索某中间件存在的历史漏洞
|
||||
|
||||
> moon.py -u exploits xxxxxx
|
||||
|
||||
|
||||
|
||||
请勿用于违法行为,后果自负。
|
||||
|
||||
6
moon.py
6
moon.py
@@ -19,6 +19,8 @@ import bf_dicts.Main_bf
|
||||
import thinkphp.Main_thinkphp
|
||||
import memcache_vuln.Main_memcache_vuln
|
||||
import js_find.Main_js_find
|
||||
import search_exploits.Main_search_exploits
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
|
||||
@@ -43,7 +45,7 @@ modul:js
|
||||
pass
|
||||
else:
|
||||
sys.argv[3] = sys.argv[3][0:-1]
|
||||
print('[*]检测地址:'+sys.argv[3])
|
||||
print('[*]目标:'+sys.argv[3])
|
||||
|
||||
if sys.argv[2] == 'tomcat':
|
||||
tomcat.Main_tomcat.exec(sys.argv[3])
|
||||
@@ -81,6 +83,8 @@ modul:js
|
||||
memcache_vuln.Main_memcache_vuln.exec(sys.argv[3])
|
||||
elif sys.argv[2] == 'js':
|
||||
js_find.Main_js_find.exec(sys.argv[3])
|
||||
elif sys.argv[2] == 'exploits':
|
||||
search_exploits.Main_search_exploits.exec(sys.argv[3])
|
||||
|
||||
else:
|
||||
print('''
|
||||
|
||||
10
search_exploits/Main_search_exploits.py
Normal file
10
search_exploits/Main_search_exploits.py
Normal file
@@ -0,0 +1,10 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
import search_exploits.search_exploit
|
||||
|
||||
|
||||
def exec(URL):
|
||||
search_exploits.search_exploit.attack(URL)
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
exec()
|
||||
1
search_exploits/__init__.py
Normal file
1
search_exploits/__init__.py
Normal file
@@ -0,0 +1 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
15
search_exploits/search_exploit.py
Normal file
15
search_exploits/search_exploit.py
Normal file
@@ -0,0 +1,15 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
import requests
|
||||
|
||||
|
||||
def attack(URL):
|
||||
print(f'[+]开始在exploitalert中搜索 {URL} 存在的历史漏洞。')
|
||||
payload = {'name': URL}
|
||||
r = requests.get("https://www.exploitalert.com/api/search-exploit", params=payload)
|
||||
for json in r.json():
|
||||
print(json)
|
||||
print(f'[+]在exploitalert中搜索 {URL} 存在的历史漏洞结束。')
|
||||
|
||||
|
||||
if __name__ == "__main__":
|
||||
attack()
|
||||
Reference in New Issue
Block a user